Can he break into my WI-FI Network by spoofing my MAC address, so the MAC filter in my router would let him through, because my neighbour would use spoofed MAC address of my tablet. How to avoid being hacked and how can I figure out that somebody hacked into my tablet or into my network. My Mac has currently been hacked. I am finding out he is getting into all my bank accounts and changing the password and even 401k and trading accts. He is also attempting to hack my girlfriends computers as well as we speak. I think he got in through a hole i had with my smart tv, google WiFi, wenmo plugs, google home, Phillips hue lights etc. Oct 11, 2013 This is a video on how to hack a Mac computer. This only works for macs as far as I know. It works by first booting into first user mode, then with 3. Five simple steps to keep your Mac safe from hackers Even Apple users need to protect their data and online privacy, and keep their device secure. As well as the security of their computer. It is not easy to tell if your computer has been hacked but it is extremely unlikely for any Mac to get hacked because they have the best security of all personal computers in the world. The only likely way to hack your Mac would be if you allowed someone to have.
Back up, wipe, reinstall, migrate in only docs, change all passwords on mail and Wi-Fi and all connected devices.
Don’t discuss trading or financials outside strictly necessary conversations, and don’t expect add-on security software or hardware products to actually do what it claims, and do expect at least some of those products to potentially open up new avenues for exploitation.
Don’t run a guest network. Or if you do need a guest network, isolate it. WPA2 with a long pre-and complex shared key,
Use a password manager.
Safari on recent releases can show shared passwords, with a warning triangle in its password store. (Safari uses Keychain for storage, but the caution marker is something that only Safari shows and nor Keychain.) Remove most or all duplicates, when you’re changing passwords everywhere.
Backups, wipe, reinstall from known-good, change all credentials, enable multi-factor authentication where that’s available.
Backups are a key part of breach recovery.
Notify your financial institutions. Also notify your local police.
Oct 27, 2018 10:00 AM
Well, you’re right, there’s someone behind your computer’s behavior. Someone with motives and tech knowledge that’s applied in favor of not-so-friendly goals.
By gaining unauthorized access to networks and computers, these criminals play very tough jokes on us. Well, that’s the best scenario probably.
The worst case? They rob personal and financial data to extort victims in exchange for money. HBO executives probably recall this.
But it’s not probable… Right?
Well… Yeah, it is. Computerworld states that at least 90% of all US-based companies have suffered an attack, while 65% of internet users globally have been a victim of some sort of cyber-crime.
If your PC has been hacked or infected with a virus, or some kind malware, you have to take quick action to protect your information and prevent the attack’s spread through your computer.
These are the three steps you should take when things go downhill and you have to scream: ****, my computer was hacked!
All hackers look like this, right?
Change your passwords
I really hope your password isn’t 12345. According to Betterbuys, “it only takes five hours to decipher a password that’s 6 basic characters long”. On the other hand, if you double the number and pick a password that’s 12 characters long, it takes two centuries.
That’s why the first step is: change your PC’s access password.
Actually, change all your passwords. I mean it. Email, social, subscriptions, etc. Every service you have access to holds precious information, including billing options that are authorized for use and personal data.
Listen to this user’s story on how he secured his Mac and arrested the thief. (Dramatized from this original story).
Intego points out that in some situations, you could be the cause that triggered the hacking. How? Well, believe it or not, you may have given your password to a hacker without noticing.
One password is enough to grant access to all sort of accounts. So double check its strength and do think it through.
Let’s up the bar and reinforce yours! According to Digicert, there are five criteria you should follow when creating a safe password.
- It needs to be at least 8 characters long
- It shouldn’t include personal information, like your name, your username, or your company’s name. Get creative with it, have fun!
- It has to be different from your previous ones.
- If possible don’t include complete words.
- Create it using characters from all four categories: lower and upper case, numbers and symbols.
Quarantine your PC
LifeWire suggests you isolate the infected computer as soon as possible. As long as you’re connected to the internet, the hacker has access to the device and its directory.
Cut the network cable! OK, no. Stop, it’s less dramatic. Simply unplug your computer from the network and avoid any kind of connection. You wouldn’t want to infect others!
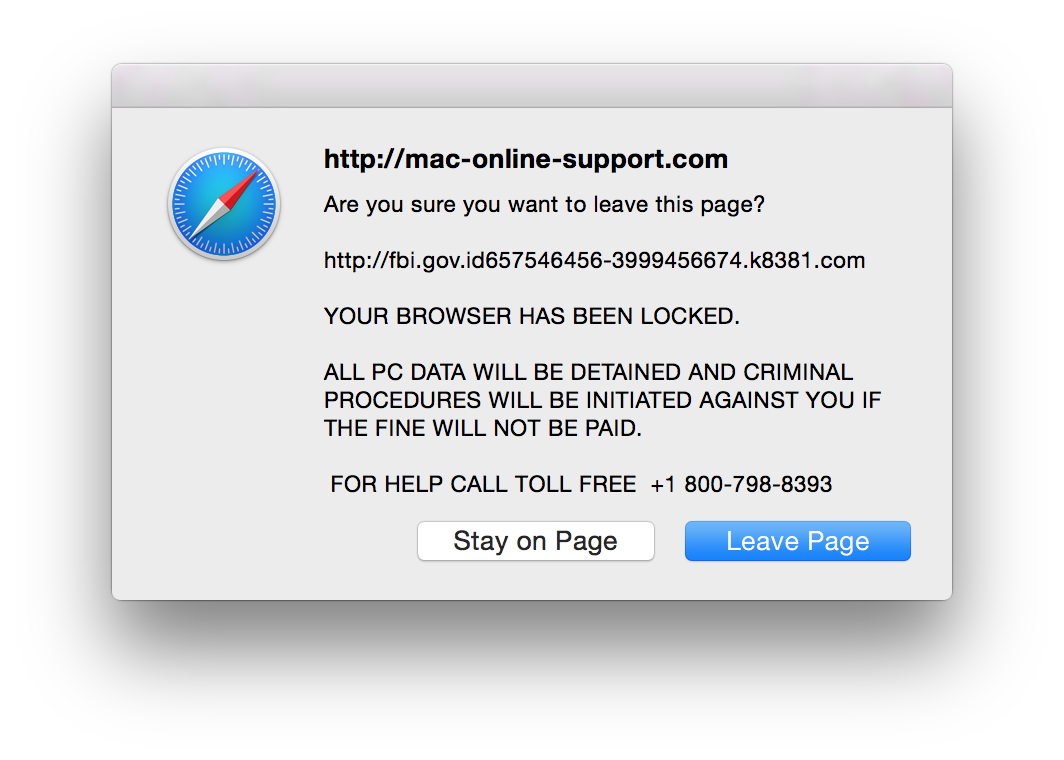
How To Know If My Computer Is Hacked Mac
PS: You take care of the cyber in cybercrime and we’ll take care of crime for you! Get your phones, tablets, and laptops protected with Prey for FREE.
Make sure you’re offline and turn all Wi-Fi connections off, both by software and hardware. Some laptops even have a switch for this.
Why hardware? Well LifeWire explains that it’s quite possible that you’re being tricked by the attackers, who would like you to think you are offline while their malware works happily in the background.
Spread the word!
Usually hackers try to spread through individual breaches, and the reason is simple: none of your friends would probably suspect from you.
So before you spam a virus to your family, friends, and coworkers… Give a heads up. Protect your core group and try to notify it immediately to avoid unpleasant situations.
Intego also explains how hackers use your email to send messages pretending to be you.
And let’s not forget about the most embarrassing outcome: when hackers post stuff in your social accounts. Yup, that sucks. They never share a good meme, it’s always a shameful day for the victim.
So, it’s pretty clear why it’s important to protect your personal and professional circle from these posts. They might make a few jokes about your browsing history, but they will also avoid falling into the same pit.
Conclusion: Be Ready
Prevention is the cornerstone of virtual security and the best defense against hackers. Turn off your computer when you’re not using it; save sensible files on portable HDDs; and don’t be afraid of data encryption.
These tips are both effective and super easy to implement.
Is My Computer Hacked Machines
Cyber-crimes are a real threat, and the methods implemented prove to be creative and accessible for anyone that has time and a reason.
Is My Computer Hacked Currently
But if you act quickly enough, you’ll have a key advantage that might make the difference when trying to recover your files and minimize the damage. Time to get ready and react!